Your gadgets may very well be mining cryptocurrency with out your data. Proper now.
At this time, there are greater than 20,000 cryptocurrencies worldwide, valued at greater than a trillion {dollars}. Mining these cryptocurrencies affords profitable returns, however it’s no straightforward activity. It requires {hardware}, uninterrupted electrical energy, and big computational energy.
A technique cybercriminals overcome this drawback of crypto mining is cryptojacking. They reap the reward, however you pay the associated fee with out even realizing it.
What’s cryptojacking?
Cryptojacking is the unlawful strategy of stealing a tool’s computational energy to mine cryptocurrencies with out the person’s data or permission.
To defend towards cryptojacking, it’s important to strengthen your cybersecurity program. It’s best to use antivirus software program, runtime software self-protection (RASP) software program, and net software firewalls (WAF) options. However to repair sturdy safety defenses, it’s essential to grasp cryptojacking intimately.
And that is what we’ll attempt that can assist you do with this text. We’ll discover the darkish world of cryptojacking and take a more in-depth take a look at the way it works. We’ll additionally discover ways to detect cryptojacking makes an attempt and what you are able to do to guard your gadgets from falling prey to this sneaky and dear cybercrime.
How does cryptojacking work?
Earlier than we dive deep into cryptojacking, let’s begin with the fundamentals of cryptocurrencies and crypto mining. That is necessary for understanding how cryptojacking works.
Cryptocurrency and crypto mining: a primer
In 2009, one mysterious developer named Satoshi Nakamoto mined Bitcoin, the first-ever digital forex. Quick ahead a decade, and the cryptocurrency market is booming.
Definition of cryptocurrency: Cryptocurrency, generally referred to as crypto-currency or crypto cash, is digital cash constructed on blockchain expertise and secured by cryptography. It’s decentralized, which means no central authority or banks regulate it. Nonetheless, all transactions are encrypted, saved, and recorded in a public database by means of blockchain expertise.
These days, we now have cryptos like Ethereum, Tether, Solana, BNB, XRP, and even Dogecoin, other than the a lot sought-after Bitcoin. Crypto fans contemplate crypto cash extraordinarily helpful, leading to hovering cryptocurrency costs for the reason that early Bitcoin days. Such excessive costs made crypto mining, the way in which to earn cryptocurrencies, extraordinarily profitable.
Definition of crypto mining: Crypto mining or cryptocurrency mining is the method of making new digital cash by verifying and including blocks to an current blockchain. Right here, verifying and including blocks contain fixing advanced cryptographic hash equations. The primary miner to crack the puzzle will get mining rewards like newly created cryptocurrencies or transaction charges.
This strategy of guessing the hash requires utilizing computational energy. The extra worthwhile a cryptocurrency is, the harder the hash is, and the extra crucial computational energy is.
At this time, crypto miners make use of crypto mining software program and highly effective laptop chips like field-programmable gate arrays (FPGAs) or specialised application-specific built-in circuits (ASICs) to mine cryptos. Another miners bundle their computing sources in mining swimming pools and share the earned income for the newly mined block.
The anatomy of cryptojacking
Now, cryptojacking is an unlawful approach of crypto mining. Hackers don’t make use of any of their very own sources. As an alternative, they steal the computing energy of an unsuspecting person by deploying cryptojacking malware onto the sufferer’s platform.
Right here, cryptojacking malware is a malicious code that illegally mines cryptocurrency on a tool with out the person’s data or permission. It may be a easy JavaScript code embedded in an internet site or malware embedded regionally on a tool.
Hackers leverage these malicious codes by way of totally different strategies, like attaching them on webpages and on-line advertisements that customers may unknowingly click on on or putting in them on the sufferer’s laptop with social engineering strategies.
- As soon as the crypto-malware is put in and activated in a tool, it immediately connects to a mining pool by way of the web or an software programming interface (API).
- The gadget receives a hash puzzle activity to resolve.
- As soon as the hash worth is calculated, it will get despatched again to the mining pool.
- As the brand new block will get added to the blockchain, the attacker will get the rewards with out spending any power or sources.
Targets of cryptojacking assaults
Hackers like to focus on these gadgets for cryptojacking assaults:
- Browsers
- Private computer systems, laptops
- On-premise servers
- Cloud servers
- Web of Issues (IoT) botnet
- Cell phones
Sorts of cryptojacking assaults
Three main forms of cryptojacking happen: in-browser cryptojacking, in-host cryptojacking, and in-memory cryptojacking. Let’s take a look at all three.
In-browser cryptojacking
A mean laptop is perhaps unable to mine cryptocurrencies. However 1000’s of common computer systems linked collectively by means of the web might do the job simply. Browser-based or in-browser crypto mining tries to do exactly that. It merely makes use of an internet site customer’s laptop to mine cryptocurrency whereas they browse.
Right here, hackers use ready-to-mine scripts from service suppliers like Coinhive or CryptoLoot, and inject the code into an internet site’s HTML supply code.
So long as the sufferer stays on-line, the mining occurs. In-browser cryptojacking turns into worthwhile when a person stays on an internet site longer than 5.53 minutes. In consequence, it is extensively present in free motion pictures or gaming web sites.
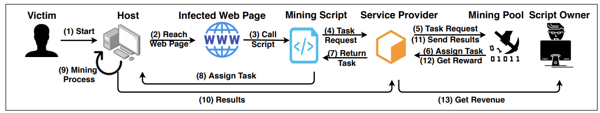
Supply: SoK: Crypotjacking Malware – arXiv
Browser-based cryptojacking noticed a large decline when CoinHive, a significant crypto mining script supplier, shuttered through the crypto market downturn in 2019. Nonetheless, researchers maintain discovering new crypto-mining scripts and web sites that use them deliberately or unintentionally.
In-host cryptojacking
In one of these cryptojacking, hackers set up crypto malware like conventional Trojan horses. For instance, an attachment of a phishing e-mail can infect a pc by loading crypto mining code immediately into the disk.
Aside from crypto mining scripts, attackers additionally modify a number of plug-and-play model mining functions like XMRig to illegally mine cryptos.
Hackers ship the malware to the host system utilizing vulnerabilities or social engineering strategies or as a payload in an unintentional obtain (the drive-by-download approach) on the host’s gadget.
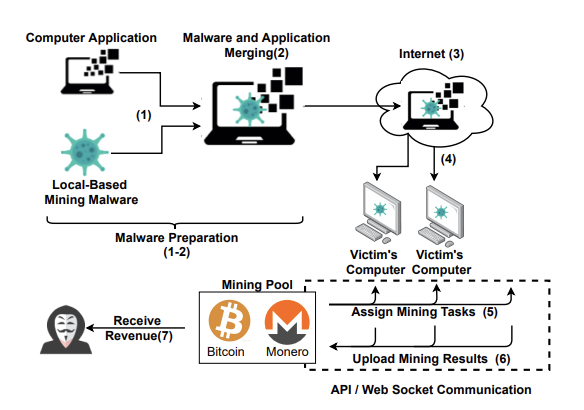
Supply: SoK: Crypotjacking Malware – arXiv
As an example, hackers lately disguised their crypto-mining malware as a desktop model of the Google Translate app. 1000’s of customers trying to find Google Translate for his or her private computer systems (PCs) downloaded it. Nonetheless, as soon as put in, it arrange a classy setup to mine Monero cryptocurrency with out the person’s data.
In-memory cryptojacking
In-memory cryptojacking makes use of the identical strategies of an infection as host-based cryptojacking. Nonetheless, cryptojacking malware is often fileless malware and runs on random entry reminiscence (RAM). It misuses official native functions or preinstalled instruments.
In consequence, the cryptojacking script doesn’t depart any footprints within the system, making it troublesome to detect and take away. As soon as attackers are inside a system utilizing fileless malware, they leverage the entry to escalate their privileges within the sufferer’s community and achieve a big pool of the sufferer’s central processing unit (CPU) sources to illicitly mine cryptos.
Since attackers can achieve command and management with this methodology, a fileless cryptojacking could be transformed to a ransomware assault, too.
Mehcrypt, as an example, is fileless cryptojacking malware. It abuses a number of official functions, like notepad.exe and explorer.exe, to hold out its cryptojacking routine.
Historical past and evolution of cryptojacking
From the early days, cryptocurrency miners developed novel methods of getting extra computational energy to mine cryptos that decreased their burden. A kind of methods was browser-based crypto mining.
When it was first launched in 2011, browser-based crypto mining was promoted as a substitute for in-browser promoting. And why wouldn’t individuals not prefer it? As an alternative of seeing intrusive advertisements on web sites, you get a clear looking expertise in return for lending your laptop to crypto miners. Easy, easy – sounds authorized, proper?
That’s what numerous different individuals thought to start with. Various crypto fans and web site house owners used in-browser mining by including mining scripts to their web sites. Nonetheless, browser-based mining was quickly abused by hackers and cybercriminals. It grew to become significantly infamous after the launch of Coinhive in 2017.
Coinhive and the rise of cryptojacking
Coinhive was a crypto mining script supplier. In 2017, it launched a easy JavaScript that mined Monero (XMR), a Bitcoin-like cryptocurrency, by using in-browser crypto mining.
Typically, JavaScript is routinely executed when an online web page is loaded. It’s platform-independent and runs on any host – PCs, cell phones, tablets – so long as the net browser operating on the host has JavaScript enabled.
In consequence, any web site might embed Coinhive JavaScript on their web site and make the web site customer’s laptop mine for them. Coinhive took 30% of the mined Monero as their payment, whereas the net web page proprietor took the remaining.
The straightforward, scalable, and low-effort methodology to roll out crypto mining to a big person inhabitants with out extra investments made it disruptive. Numerous crypto fans readily adopted its code.
Nonetheless, whereas Coinhive’s enterprise mannequin was touted as authorized, its code was quickly abused. Some web site house owners hijacked customers’ processing energy with out their permission to mine XMR utilizing the Coinhive script.
Along with web site house owners, malicious actors hacked and embedded the crypto mining code on high-traffic web sites. In addition they put in the script on browser extensions like Archive Poster and web site plugins like Browsealoud.
By way of these strategies, Coinhive’s code discovered its approach illegally to common web sites of corporations like Showtime, The Los Angeles Occasions, Blackberry, and Politifact. They ran in-browser crypto mining with out permission and generally with out the web site proprietor’s data, successfully hijacking the positioning and the person’s laptop sources. Even the web sites of the US, UK, and Indian governments’ web sites had been discovered to be affected by these cryptojacking assaults.
It must be famous that mining cryptocurrencies with the computing energy of others shouldn’t be thought-about unlawful when a transparent notification of actions is proven and the opportunity of opting out exists for customers. Nonetheless, most in-browser crypto mining lacks these and is due to this fact thought-about unlawful.
The rising situations of illicit crypto mining from 2017 introduced cryptojacking to mainstream consideration. Cybercriminals began utilizing not solely unlawful browser-based crypto mining but in addition malware and different strategies for unlawful crypto mining.
Current cryptojacking assault examples:
- Kiss-a-dog was a cryptojacking marketing campaign focusing on susceptible Docker and Kubernetes infrastructures to mine Monero utilizing XMRig.
- Mexals, who name themselves Diicot, launched a cryptojacking marketing campaign by means of a safe shell (SSH) brute-force assault and mined over $10,000 price of Monero cash.
- ProxyShellMiner is a crypto-mining malware that exploits the unpatched vulnerabilities in Microsoft Trade servers.
- 8220 Gang, a cybersecurity menace actor, scans the web for susceptible cloud customers, absorbs them into its cloud botnet, after which distributes cryptocurrency mining malware.
- Headcrab, a crypto-jacking malware, has contaminated over 1,000 Redis servers to construct a botnet that mines Monero
- In October 2024, a cryptojacking assault focused Docker Engine APIs by exploiting weak safety settings. The attackers used these vulnerabilities to manage Docker programs and run software program that mines Monero cryptocurrency.
Why do some crypto miners cryptojack?
Contemplate this. In 2009, a PC with an Intel Core i7 processor might mine round 50 bitcoins each day. However at present, we’d like specialised mining rigs like ASIC programs to mine cryptos like Bitcoin.
Additional, many cryptocurrencies even have limits on what number of cash could be mined and the reward that miners get. Add to this combination hovering power costs. A single bitcoin requires 811.90 kilowatt-hours, equal to the common quantity of power consumed by an American family in 28 days. All this makes crypto mining a expensive affair. At this time, mining Bitcoin at residence shouldn’t be even an possibility.
In such a state of affairs, turning a revenue from crypto mining with official sources may very well be troublesome. In consequence, hackers attempt to offload the associated fee to others by hijacking a sufferer’s system.
Why do you have to care about cryptojacking?
Forewarned is forearmed. It’s higher to know the hazards of cryptojacking and be ready than fumble once you face an precise assault.
In contrast to many different cybersecurity threats that announce their presence, cryptojacking succeeds in full silence.
Amal Joby
Cybersecurity Analysis Analyst, G2
What’s extra regarding is attackers at present goal gadgets with extra processing energy reasonably than private gadgets. Some examples are enterprise cloud infrastructures, servers, a lot of inadequately protected IoT gadgets, or Docker and Kubernetes containers. With this, the attackers goal to acquire extra revenue in much less time.
This has wide-ranging implications for enterprises. For each greenback created from crypto-jacking, the sufferer will get billed $53. The danger doesn’t cease with inflated payments. As soon as contained in the enterprise infrastructure, attackers can leverage their entry at any time to hold out different harmful cyber assaults, equivalent to ransomware and provide chain assaults.
Easy methods to detect cryptojacking assaults
Cryptojacking assaults are sometimes hidden however not unidentifiable. Attempt a few of these strategies to detect cryptojacking assaults.
Easy methods to detect cryptojacking assaults in gadgets
In the event you discover the next indicators in your PC or cell gadget, your gadget could have been cryptojacked.
Deteriorating efficiency
Cryptojacking causes your gadget to considerably decelerate or crash often. In the event you begin noticing unusually poor gadget efficiency, scan your system utilizing antivirus software program to see for those who discover any cryptojacking malware.
Overheating
One other telltale signal of cryptojacking is overheating. Since cryptojacking consumes an excessive amount of processing energy, it simply overheats a system and drains the battery. You may discover followers operating sooner than ordinary to chill the gadget. Or your cell phone battery may present poor efficiency and drain quickly resulting from overheating.
CPU utilization
One other noticeable symptom is excessive CPU utilization. Computer systems maintain information of all of the operating functions within the system. In the event you discover a spike in CPU utilization whereas doing a small activity or looking an innocuous web site, it could be due to cryptojacking.
A fast cryptojacking check in your gadget!
To verify CPU utilization:
- In Home windows, open Activity Supervisor > Efficiency > CPU.
- On a Mac, go to Purposes > Exercise Monitor.
You must also verify if there’s an software that has elevated web visitors greater than regular, which might point out in-browser mining. To verify this:
- In Home windows, go to Settings > Community & Web > Information Utilization > View utilization per app.
- For Apple customers, go to the Exercise Monitor > Community > Despatched Bytes.
Be aware that criminals have give you refined evasion strategies to cover spikes in CPU utilization or web visitors.
Easy methods to detect cryptojacking assaults in a cloud surroundings
Detecting cryptojacking is perhaps troublesome if corporations have decrease visibility into their cloud utilization. Nonetheless, companies can attempt to work round this.
Audit cloud entry controls
A lot of the cyberattacks on the cloud originate from the misconfigured cloud, so audit your entry controls. Any insecure or misconfigured entry to your cloud surroundings could be additional investigated to see if there’s been any malicious exercise like illicit crypto mining.
Analyze cloud community logs
Community logs monitor visitors to and out of your cloud and present you the present state of the community and who’s connecting from the place. Analyze these information. You’ll acknowledge any irregular community habits or a sudden spike in visitors, which may very well be an indication of a bootleg crypto miner operating in your cloud surroundings.
Monitor cloud spend
Inflated cloud payments are indicators of both legitimately elevated utilization of cloud sources out of your finish or somebody stealing your cloud sources for his or her revenue. In the event you don’t have any cloud mismanagement in your finish, examine any spike in cloud payments to see if it’s associated to cryptojacking.
To be clear, all these strategies let you know in case your cloud has been compromised in any approach. Additional evaluation of any malicious exercise must be finished to find out whether or not the compromise is because of unlawful crypto miners or another cyber assault.
Suggestions for shielding your gadget towards cryptojacking assaults
Prevention is healthier than treatment, so use these sensible tricks to safeguard your programs towards cryptojacking assaults.
- Use a powerful antivirus program to detect any malicious exercise or malware.
- Make use of anti-crypto mining extensions like Miner Block and Anti-Miner to forestall browser-based crypto mining.
- Set up advert blockers to dam undesirable pop-up advertisements and banner advertisements on web sites. Crypto mining malware is commonly embedded in advertisements.
- Replace your system and set up all the newest software program to patch vulnerabilities.
- You may as well disable JavaScript in your browser to forestall malicious scripts from loading. Nonetheless, it will cut back person expertise.
Steps to disable JavaScript in your Chrome browser:
- Go to Settings > Privateness and Safety > Web site settings > JavaScript
- Choose the Don’t enable websites to make use of JavaScript choice to disable JavaScript.
For enterprises, stopping cryptojacking assaults goes past protecting these primary steps. Undertake the next safety practices to guard your IT belongings towards illicit crypto mining.
- Set up firmware updates and patches: Replace your system software program as quickly because the software program vendor releases them.
- Have a strong id and entry administration (IAM) coverage. An efficient IAM protects towards unauthorized entry to your system, on-premise or in the cloud. Deploy IAM software program to permit entry solely to approved customers and handle their degree of clearance.
- Safe your endpoints. Finish-user gadgets like laptops, workstations, servers, and cell phones function factors of entry to your company community. Defend them utilizing sturdy endpoint safety software program to cease malicious software program from infecting them. You possibly can even use cell knowledge safety options to safe entry to your enterprise’s community by way of cell gadgets.
- Monitor your community. Fastidiously analyze all of your community logs in actual time and search for malicious exercise. Depend on instruments like WAF and safety data and occasion administration (SIEM) software program to get direct visibility into your community and endpoint and detect any irregular habits or unauthorized utilization. Leverage RASP instruments to detect and forestall assaults in actual time in your software runtime surroundings.
- Deploy cloud safety options. You should utilize extra cloud safety options, equivalent to cloud entry safety dealer (CASB) software program for cloud entry management and cloud safety posture administration (CSPM) software program, to search for cloud misconfigurations.
- Prepare your workers. Undertake cybersecurity coaching applications in your workers and maintain them conscious of social engineering assaults like phishing.
- Undertake the zero-trust mannequin. Belief nobody. Confirm every part. Having a zero-trust strategy to your safety means you explicitly confirm anybody or something that seeks entry to your IT belongings. This goes a good distance in defending your system towards any cyber menace.
Block the unlawful block
Cryptojacking assaults have gotten extra prevalent and troublesome to detect whilst crypto costs fluctuate. Hackers are getting extra refined with their an infection and evasion strategies, however prevention is the important thing. Implement the safety practices shared right here and keep one step forward of crypto thieves.
Discover menace intelligence software program to maintain your safety crew up to date on rising malware and zero-day vulnerabilities.
This text was initially revealed in 2023. It has been up to date with new data